Privacy laws are being passed in more and more states every year. Even non-healthcare businesses are finding they must follow privacy laws in the states they do business in. Conducting a privacy assessment is a great way to understand what data you have that needs protecting, what things can go wrong and then, of those things that can go wrong, which ones we can try to prevent.
In this episode:
Privacy Assessments – Ep 370
Today’s Episode is brought to you by:
Kardon
and
HIPAA for MSPs with Security First IT
Subscribe on Apple Podcast. Share us on Social Media. Rate us wherever you find the opportunity.
The Privacy and Security Boot Camp
What had happened was….
Stay tuned here for updates when new dates are set.
Great idea! Share Help Me With HIPAA with one person this week!
Learn about offerings from the Kardon Club
and HIPAA for MSPs!
Thanks to our donors. We appreciate your support!
If you would like to donate to the cause you can do that at HelpMeWithHIPAA.com
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
If you see a couple of numbers on the left side you can click that and go directly to that part of the audio. Get the best of both worlds from the show notes to the audio and back!
HIPAA Say What!?!
[09:02] How to use Chromebooks securely in healthcare? Chromebooks are, by default, much more secure than other operating systems. The operating system running them is very closed off. Chromebooks do allow you to store things on them. In order to use them in healthcare, you first need to determine what it is you’re going to be doing on them and how they are going to be used. If you are going to be storing files in Google Drive that contain PHI, you will need a business associate agreement with Google.Now, Chromebooks do not technically have antivirus and other security programs like that on them, but the security provided within the Chromebooks is pretty solid. So, you can use them securely in healthcare, but you need to make sure that the account that is managing these Chromebooks is very well protected so that somebody can’t get into that account and then manage those Chromebooks for themselves.
405(d) Tip of the Week
[17:07] The 405d task force is a part of a large interrelated group of organizations, including the Healthcare and Public Health Sector Coordinating Council (HSCC) and the Health Sector Cybersecurity Coordination Center (HC3). HC3 released an alert in the last couple of weeks about a malware spam (malspam) campaign currently targeting various health care providers.HC3: Sector Alert – Secure Message/Evernote Themed Phishing Campaign
Basically, people had their email compromised, their addresses and all of their information got downloaded. And they’re using that data, they believe, to be able to customize these emails to make them more tricky so that it’s easier to victimize you.
For more information on this, check out this article – Feds Warn Healthcare Entities of ‘Evernote’ Phishing Scheme from HealthcareInfoSecurity.
How do I do a privacy assessment?
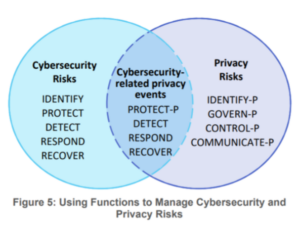
[21:41] Privacy assessments are very important but most people don’t even realize they should do them. These assessments look at more than a HIPAA assessment would evaluate. You can narrow it down to PHI or open it up to all privacy concerns. For this exercise, at least the first pass, including everything, would make it easier in the long run.The best way to get started working with specific Privacy concerns is to tap into the NIST Privacy Framework guides. It is very familiar to anyone who uses NIST CSF and is designed to work in conjunction with the CSF.
The identify function is where the assessments are included very much like they are in the CSF version of the identify function. Let’s review what those requirements are as they are listed in the privacy framework. Here is what is listed in the guide. Listen to the podcast for our interpretations and recommendations for each of them.
Inventory and Mapping (ID.IM-P): Data processing by systems, products, or services is understood and informs the management of privacy risk.
- ID.IM-P1: Systems/products/services that process data are inventoried.
- ID.IM-P2: Owners or operators (e.g., the organization or third parties such as service providers, partners, customers, and developers) and their roles with respect to the systems/products/services and components (e.g., internal or external) that process data are inventoried.
- ID.IM-P3: Categories of individuals (e.g., customers, employees or prospective employees, consumers) whose data are being processed are inventoried.
- ID.IM-P4: Data actions of the systems/products/services are inventoried.
- ID.IM-P5: The purposes for the data actions are inventoried.
- ID.IM-P6: Data elements within the data actions are inventoried.
- ID.IM-P7: The data processing environment is identified (e.g., geographic location, internal, cloud, third parties).
- ID.IM-P8: Data processing is mapped, illustrating the data actions and associated data elements for systems/products/services, including components; roles of the component owners/operators; and interactions of individuals or third parties with the systems/products/services.
- ID.BE-P1: The organization’s role(s) in the data processing ecosystem are identified and communicated.
- ID.BE-P2: Priorities for organizational mission, objectives, and activities are established and communicated.
- ID.BE-P3: Systems/products/services that support organizational priorities are identified and key requirements communicated.
- ID.RA-P1: Contextual factors related to the systems/products/services and the data actions are identified (e.g., individuals’ demographics and privacy interests or perceptions, data sensitivity and/or types, visibility of data processing to individuals and third parties).
- ID.RA-P2: Data analytic inputs and outputs are identified and evaluated for bias.
- ID.RA-P3: Potential problematic data actions and associated problems are identified.
- ID.RA-P4: Problematic data actions, likelihoods, and impacts are used to determine and prioritize risk.
- ID.RA-P5: Risk responses are identified, prioritized, and implemented
If we are only going to worry about a HIPAA privacy assessment, then you’re looking at more of the big issues that people get wrong. So, things like right of access, the NPP and can you prove you’re following your privacy policies and procedures. Then you do a deep dive into what the policies say to determine whether you can prove you are following them.
So there you have it. Overall, a privacy assessment involves identifying all the data you have, defining where it is stored, who can get to it and then look at what can go wrong and how you feel about it. Only then will you be able to create a plan or adjust your plan to protect it.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
HIPAA is not about compliance,
it’s about patient care.TM
Special thanks to our sponsors Security First IT and Kardon.