
In the world of cybersecurity, small businesses have their own set of unique challenges. As AI technology becomes more common, using AI in cybersecurity sounds promising, but it’s crucial to handle it wisely to avoid new risks. These tools are powerful, but they need to be used carefully because they can also open up new kinds of cyber threats. Small businesses need to build a strong culture of security, making sure everyone is up to speed and constantly testing their defenses against attacks. It’s also vital for them to keep their security practices flexible to stay ahead of new threats and tech developments.
In this episode:
AI Plus Small Business Cybersecurity – Ep 455
Today’s Episode is brought to you by:
Kardon
and
HIPAA for MSPs with Security First IT
Subscribe on Apple Podcast. Share us on Social Media. Rate us wherever you find the opportunity.
Great idea! Share Help Me With HIPAA with one person this week!
Learn about offerings from the Kardon Club
and HIPAA for MSPs!
Thanks to our donors. We appreciate your support!
If you would like to donate to the cause you can do that at HelpMeWithHIPAA.com
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
If you see a couple of numbers on the left side you can click that and go directly to that part of the audio. Get the best of both worlds from the show notes to the audio and back!
Thanks to our donors.
HIPAA Briefs
[05:57] Change Healthcare Ransomware attack goes from bad to worseChange Healthcare’s ransomware fiasco is constantly going from bad to worse, as now a new threat actor has emerged with ransom demands in exchange for the stolen data.
Roughly a month and a half after initially detecting an attack, a different threat actor going by RansomHub is claiming to own the stolen data, and is asking Change Healthcare for more money. If the company doesn’t follow through, it will sell it to the highest bidder.
According to Wired, which saw screenshots of the database, confirming the authenticity of the database is difficult, but it all points to the data being authentic. The RansomHub threat actor is apparently associated with an individual going by “Notchy”, who was the one to originally get duped by ALPHV.
Attribution: Yet another hacker group demands ransom from Change Healthcare | TechRadar
405(d) Tip of the Week
[08:46] A couple of weeks ago the 405(d) folks dropped a new Healthcare Threat Identification poster. Check it out:New Resource: Healthcare Threat Identification Poster
These free resources and perfect training tools for your organization.
ISAC: HC3 Alert
[10:21] Social Engineering Attacks Targeting IT Help Desks in the Health Sector“HC3 has recently observed threat actors employing advanced social engineering tactics to target IT help
desks in the health sector and gain initial access to target organizations. In general, threat actors continue
to evolve their tactics, techniques, and procedures (TTPs) to achieve their goals. HC3 recommends various
mitigations outlined in this alert, which involve user awareness training, as well as policies and procedures
for increased security for identity verification with help desk requests.”
AI Plus Small Business Cybersecurity
[16:06] Cyber Guidance for Small Businesses | CISAThe opening paragraphs put it bluntly.
This advice is different.
Below, we offer an action plan informed by the way cyber-attacks actually happen. We break the tasks down by role, starting with the CEO. We then detail tasks for a Security Program Manager, and the Information Technology (IT) team. While following this advice is not a guarantee you will never have a security incident, it does lay the groundwork for building an effective security program.
If you are just getting started you should get this done and while you are doing it add AI risk management to the mix. Let’s review what the recommendations are from CISA and how to add in some of the NIST guidance for managing AI while you are at it. If you already have a cybersecurity program in place then review the details from CISA and add in the NIST AI while you are at it.
NIST AI Resources
Artificial Intelligence Risk Management Framework (AI RMF 1.0)
NIST AIRC – AI Risks and Trustworthiness
Role based action plans help sort out who needs to do what. Note, it is not an IT problem or IT’s job to handle the whole thing. This just scratches the surface for what should be done if you are in healthcare – CISA’s guide is for all small businesses and does not address the requirements of regulations for any industry.
CEO’s set the tone
[29:57] “Cybersecurity is about culture as much as it is about technology.” That’s the point that has to come across first. Until that happens nothing will change. Period. We discussed changing culture and setting it from the top so many times over the 4 days we held our boot camp last week. If that fails then most everything else will fail. The key here is just 4 words: “Culture cannot be delegated.” This is the reason everything must begin with the CEO setting the tone that it is non-negotiable – security must be addressed constantly.The number one thing CEOs must do is stated very well:
- Establish a culture of security. Make it a point to talk about cybersecurity to direct reports and to the entire organization. If you have regular email communications to staff, include updates on security program initiatives. When you set quarterly goals with your leadership team, include meaningful security objectives that are aligned with business goals. Security must be an “every day” activity, not an occasional one. For example, set goals to improve security of your data and accounts through the adoption of multi-factor authentication (MFA) (more on that below), the number of systems you have fully patched, and the number of systems that you backup.
All the remaining tasks are for naught if that one isn’t done but here are the remaining ones in the list for CEOs
- Select and support a “Security Program Manager.” – Not an IT or security expert but ok if they have those skills also. This person is the one that makes sure the program is in place and operational at all times. That does NOT mean they are the ones doing all of the work. Note the support part of the task also.
- Review and approve the Incident Response Plan (IRP). This is your left of boom. If you haven’t done that then boom creates nothing but chaos. That isn’t to say there will be no chaos though. Boom is by definition chaotic.
- Participate in tabletop exercise drills (TTXs). Take the time to discuss the what ifs of your plan and see how the team will respond before problems occur while considering the problems that will occur.
- Support the IT leaders. When these leaders need support it must come from the CEO for it to stick. That doesn’t mean just doing whatever they say, though. It means supporting their implementation but evaluating it constantly. They are in the weeds, you are the leader. That is how it is supposed to work.
Consider AI now and in every meeting moving forward reviewing security or discussing technology. Ask the questions now about AI and what tools are being used or considered for use in the organization. Understand the risks that AI brings to all organizations and insist that your team invests in vetting and understanding these tools, not just jumping in feet first. Definitely, don’t avoid at all costs either or you will be left behind. Learn about the things to consider based on the NIST 3 AI Risks and Trustworthiness.
Characteristics of trustworthy AI systems include: valid and reliable, safe, secure and resilient, accountable and transparent, explainable and interpretable, privacy-enhanced, and fair with harmful bias managed.
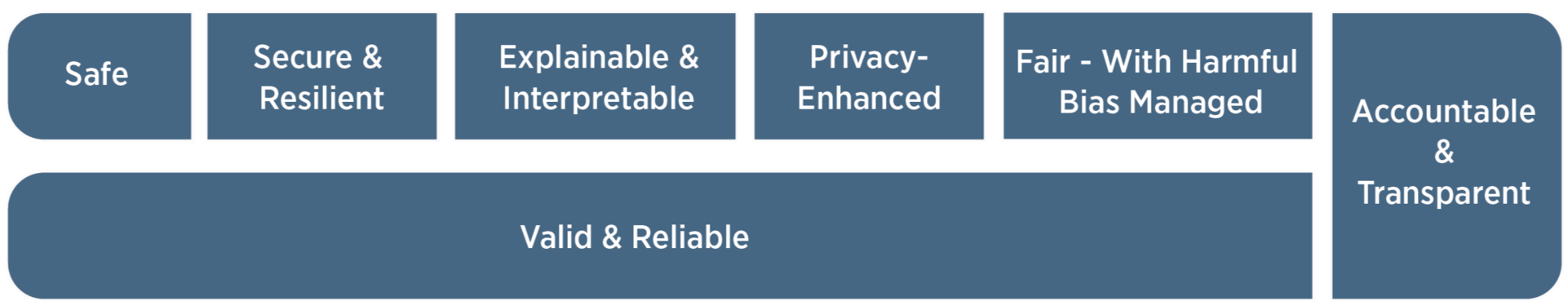
Implementing AI at a rapid pace should not result in negligence of the potential for incredibly destructive risks the tools bring to the table. Note, they should always be considered tools, not some autonomous solution where you just trust it. Ask about the tools meeting these objectives.
Security managers (or officers) steer the ship.
[47:48] Driving the program and making recommendations requires a constant level of diligence but not a constant level of completing all the plans. Make sure things are happening and moving forward with everyone on the team cooperating. Otherwise, ask for help.Here are the tasks assigned for making sure that basics are happening.
- Training. Make sure everyone is trained to understand the importance of security in the company culture. Then, make sure they know how to follow the processes and use the technology to make that happen.
- Write and maintain the Incident Response Plan.
- Host quarterly TTXs
- Ensure MFA compliance.
To make sure all of that is happening you follow the guidelines for governance and risk management. While the list above seems simple once you start doing the work you will understand the importance of having guidance and frameworks to use.
AI tools may seem like a quick solution. You can not allow that to become the case. Begin immediately evaluating all AI tools in use or under consideration within the organization. Ask about your supply chain also. A completely necessary step to manage risk is to understand what you have in place and properly vet anything you plan to change or add. Inventory AI now when you inventory everything else.
Learn the characteristics of trustworthy AI systems. Ask the questions and spend time learning about all the new tech these tools offer but don’t ignore the risks. Inform up and down the chain of command. Ask questions sideways if needed.
IT leads handle the details.
[51:19] Now we get to the actionable controls. Not just turning on some setting and assuming all is good. There must be evaluation and constant diligence for anomalies and unmanaged risks. Here is the task list for IT lead and staff.- Ensure MFA is mandated using technical controls, not faith.
- Enable MFA for all system administrator accounts.
- Patch.
- Perform and test backups.
- Remove admin privileges from user laptops
- Enable disk encryption for laptops.
Just like the other roles in the list you should be alert for AI tools creeping into the organization that are not vetted and fully understood. Don’t fall for them yourself either. Evaluate and monitor for problems just like any other solution that assists you in doing your job.
Learn the characteristics of trustworthy AI systems. Ask the questions and spend time learning about all the new tech these tools offer but don’t ignore the risks. Inform up and down the chain of command. Ask questions sideways if needed. Yes, this is a redundant paragraph on purpose.
Small businesses need to stay on their toes when it comes to cybersecurity, especially as AI starts to play a bigger role. It’s all about striking the right balance between using new tech to protect your business and being cautious not to open up new vulnerabilities. Regular training, a solid security-first mindset across the company, and staying adaptable are key. By being proactive and vigilant, small businesses can safeguard themselves against the evolving landscape of cyber threats.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
HIPAA is not about compliance,
it’s about patient care.TM
Special thanks to our sponsors Security First IT and Kardon.


