It happens out of the blue. You get a letter that tells you that there has been a complaint filed and an investigation has been opened by OCR. That may not be the best day of your life. Just the thought of opening one of those letters can make some people feel queasy. If you have ever experienced that moment where you learn, add OCR investigations to your list then you don’t have it high on your lists of things to do again. Let’s review the kinds of things you may be asked to answer when under an investigation.

In this episode:
OCR Investigations – What do they ask
Today’s Episode is brought to you by:
Kardon and HIPAA for MSPs / Security First IT
Where to meet us
- 4medapproved Healthcare Cybersecurity Officer Live Webinar Workshop – June 20, 21, 27, 28, 2018
Next HIPAA Boot Camp
Live in Tucker, GA
July 19 and 20th
Want to be part of Help Me With HIPAA? Donate to the cause at www.HelpMeWithHIPAA.com/give
HMWH App now has more features. You can now access a PDF with the show notes ready for your HIPAA training documentation! Find it under the bonus feature in the app for both the Apple and Android versions. It is a little gift box on the app bar.
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
[4:43]
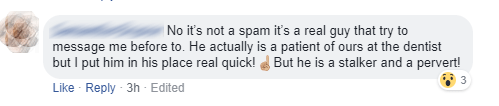
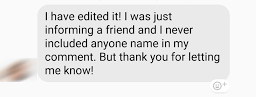
David saw this on his Facebook feed last week:
After David informed the person that this was a no-no, they still did not see the harm in it. Train your people, folks!
 🙂
🙂
OCR Investigations – What do they ask?
First, we should point out that there are statistically two ways you are most likely to have an investigation. You report a data breach to HHS or someone files a complaint about your business with HHS. Cases that happen because someone files a complaint are the most disturbing. You don’t see those coming at all.
More people are getting educated about their privacy rights and HIPAA which means more people are filing complaints. But, another source of complaints are employees current or previous with a grudge. Business competitors who may learn of a case and encourage someone to report you. We are even aware of vendors who file a complaint about their clients. At least, with a data breach, you know something went wrong and a letter may be arriving. With these, you don’t know where or when they may come.
Earlier this week, I got a call from a practice looking for “help with their HIPAA program”. 🙂 They had a complaint filed over a social media thing and got the investigation letter. The comment made after she told me that is what prompted this episode.
“Our lawyer thinks the issue on the complaint is not a problem. But, they look into everything, not just that one issue. We are missing a lot of documentation that had nothing to do with the complaint.”
Here are some examples of statements and data we have seen on OCR investigations.
The Realization Letter
When a letter shows up they start out so nice. It may have the polite words in there but the feeling you get is not a warm and fuzzy one.
Please be advised that the US. Department of Health and Human Services (HHS), Office for Civil Rights (OCR), received a complaint on X date, alleging that your company is not in compliance with the Federal Standards for Privacy of Individually Identifiable Health Information and/or the Security Standards for the Protection of Electronic Protected Health Information (45 CPR. Parts 160 and 164, Subparts A, C, and E, the Privacy and Security Rules), and the Breach Notification Rule Subpart D – Notification in Case of Breach of Unsecured Protected Health Information (PHI) (45 CFR. §§ 164.400-164.414).
Specifically, the Complainant alleged that {something has happened and they know about it}
These allegations could reflect potential violations of:
- 45 C.F.R. §164.308(a)(1)(i): Security Management Process
- 45 CPR. § I64.308(a)(1)(ii)(A): Risk Analysis
- 45 CPR. §164.308(a)(1)(ii)(B): Risk Management
- 45 C.F.R. §164.308(a)(2): Assigned Security Responsibility
- 45 CPR. §I64.308(a)(4): Information Access Management
- 45 CPR. §I64.308(a)(5)(i): Security Awareness and Training
- 45 C.F.R. §I64.308(a)(6): Security Incident Procedures
- 45 CPR. §164.308(a)(6)(ii): Response and Reporting
- 45 CPR. § l64.308(b): Business associate contracts
- 45 C.F.R. §164.312(a): Access Controls
- 45 CPR. § 164.312(a)(2)(iv): Encryption and Decryption
- 45 C.F.R. § 164.312(e): Transmission Security
- 45 C.F.R. § 164.502(a): Permitted Uses & Disclosures
- 45 C.F.R. § 164.502(b): Minimum Necessary Standard
- 45 C.F.R. § 164.504(e): Business Associate Contracts
- 45 C.F.R. § 164.520: Notice of Privacy Practices for PHI
- 45 C.F.R. § 164.530(a): Personnel Designations
- 45 C.F.R. § l64.530(b): Training
- 45 C.F.R. § 164.530(c): Safeguards
- 45 C.F.R. § 164.530“): Mitigation
- 45 C.F.R. § 164.402: Breach Risk Assessment
- 45 C.F.R. § 164.404: Notification to Individuals
- 45 C.F.R. § l64.404(d)(2): Substitute Notice
- 45 C.F.R. §164.406: Notification to the Media
- 45 C.F.R. §164.408: Notification to the Secretary
Please submit to your investigator your responses to the enclosed data request within 14 business days from receipt of this letter, and please number each response to correspond with the number in the data request. Please be sure to produce the documents in compliance with the requests set forth herein, including no staples or double-sided pages. Electronic copies are preferred.
If we are unable to resolve this matter voluntarily. and if OCR‘s investigation results in a finding that the covered entity has failed to comply with the applicable provisions of the Privacy and Security Rules and/or the Breach Notification Rule, HHS may initiate formal enforcement action which may result in the imposition of civil money penalties, or take other actions consistent with OCR‘s jurisdiction. We have enclosed a separate fact sheet explaining the penalty provisions under the Privacy, Security, and Breach Notification Rules. The fact sheet also explains that certain violations of the Privacy and Security Rules may be subject to criminal penalties, which the US. Department of Justice is responsible for enforcing.
Investigation after a breach report
These are some of the specifics they have asked for before relating directly to the case or the breach that prompted the investigation. Your specific case will have some direct part of the law that you have supposedly violated in the complaint. In a breach, they also ask specifics based on what you reported to them.
Provide a copy of the investigative report, a written description of the Covered Entity’s response to mitigate the issue, and any corroborating documentation, such as investigative reports, police reports, etc.
Please provide a copy of the notification letters sent to the affected individuals. Please also indicate if substitute notice was provided, and evidence of such notice. The evidence should indicate that notice was provided without unreasonable delay and within the requirements of 45 C.F.R. §164.404. Please provide written explanation for any delay in notification.
Please provide policies and procedures that are required by 45 C.F.R. § 164.502(a) to protect patient protected health information from impermissible uses and disclosures. Please indicate the dates of implementation and any redrafting.
Please describe the Covered Entity’s method for assigning and enforcing appropriate access to PHI in compliance with 45 C.F.R. § 164.514(d). Please produce documentation of such method, including policies and procedures. Please indicate the date of implementation and any redrafting.
Generally requested for most investigations
Many people then learn that any OCR investigation can look at any parts of your compliance program and they will often do so. The number of cases and audits that find failures in certain areas make it obvious that more evaluations are likely to uncover more failures.
Please provide policies and procedures in place regarding the Covered Entity’s training procedures pursuant to 45 C.F.R. § 164.530(b). Please indicate the dates of implementation and any redrafting. Please submit a copy of all training documents and materials developed to comply with this section. In addition, please produce documentation of the workforce’s completion of required training at the time of the incident and currently.
Please submit a copy of the CE’s most recent risk analysis, as well as a copy of all risk analyses performed for or by CE within the past 6 years pursuant to 45 C.F.R. §164.308(a)(1)(ii)(A). If no risk analysis has been performed, please provide a written description of the circumstances.
Please submit a copy of the risk management plans associated with each risk analysis requested above. These risk management plans should describe the security measures implemented by CE to sufficiently reduce the risks and vulnerabilities identified in the risk analyses to a reasonable and appropriate level to comply with §164.308(a)(1)(ii)(B).
Please provide the following:
- Current balance sheets;
- Current income statements;
- Cash flow statements;
- Most recent full year audited financial statement prepared by an independent accounting firm, (including footnotes);
- Disclosure of expenses and amounts paid/accrued to the home office and/or other related entities;
- Schedule showing amounts due to/from related companies, or individuals, included in the balance sheets. The schedule should list the names of related organizations, or persons, and indicate where the amounts appear on the balance sheet (e.g., Accounts Receivable, Notes Receivable, etc.);
- Past 2 years of tax returns; and
- Any financial disclosure statements
Expect more to come
Finally, don’t think just one request is all that will happen. Often there are at least two if not more rounds of information requested. The additional ones will ask specific questions about the information you already provided and other things those answers may bring up.
Even if you have all of this information, the time to collect it and respond appropriately is not a few minutes. The costs for doing so are also not cheap if you don’t have coverage for the attorney, consultants, etc. OCR investigations are not a quick response letter kind of project. At least, if you take them seriously they take some serious time.
For those of us that have been lucky enough to have never been on the receiving end of one of these letters, it seems scary. For those who have experienced it, they still recall the stress it created for them. Be prepared for a letter to show up out of the blue one day. It is the only way to save yourself stress, time, and money when it does happen. Again, this is simply risk management. Some people are still willing to “risk it” and deal with one of the OCR investigations if they happen. Are you?
Please remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!