 Maturity is something we expect from respected folks or grown folks but what about your privacy and security program, do you check it’s maturity? You have all of these plans, policies, procedures, and training but is it actually meeting your needs? Time to talk maturity assessments.
Maturity is something we expect from respected folks or grown folks but what about your privacy and security program, do you check it’s maturity? You have all of these plans, policies, procedures, and training but is it actually meeting your needs? Time to talk maturity assessments.
In this episode:
Maturity Assessments – Ep 206
June 13 Lunch and Learn with Medicus IT about Patient Record Release and Fees for Medical Practices – Link to register on the website.
Attending SecureWorld Atlanta – May 29/30 message me if you are going to be there.
Next HIPAA Boot Camp
Session #3 TBD
Somewhere and sometime after Labor Day
www.HelpMeWithHIPAA.com/bootcamp
Share us with one person this week!
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
Maturity Assessments
Some people who know us may say that the two of us are the least qualified to judge maturity levels. However, we know they don’t really mean that. We are mature, where it matters anyway and privacy and security is where it does matter.
There are many different frameworks or plans out there for maturity models. The NIST CSF has the Implementation Tiers. SANS, C2M2, SecureWorks, and many other names exist with recommendations. The point is there should be an assessment of how well you are doing with your program. As privacy and security become part of your day-to-day activity and company culture you will want to know what works and what needs to be improved.
Maturity of security awareness
SANS has a very simple list to reflect how aware your organization really is concerning security requirements. You start at the bottom with level 1 and proceed to 5 as your program matures. Unfortunately, level 2 is compliance focused. That means all of those programs that worry about checking the box for compliance and HIPAA made easy approaches will get you no higher than level 2 without more work.
Here is how Lance Spitzner, Director, SANS Security Awareness, explained levels 1 and 2:
Notice this scale is talking about security awareness of the organization as a whole. It assumes there are already policies and procedures in place. But, we know there are plenty of groups that think they are at level 2. But, we know there are plenty of groups that think they are at level 2. But, if you don’t have any written policies and procedures that are actually followed by staff it is hard to say you have made it that far. In the level 1 description he said “people do not know or understand organizational policies and procedures” and in order to get past that one element of level one you must have them, use them, and make people aware of them.
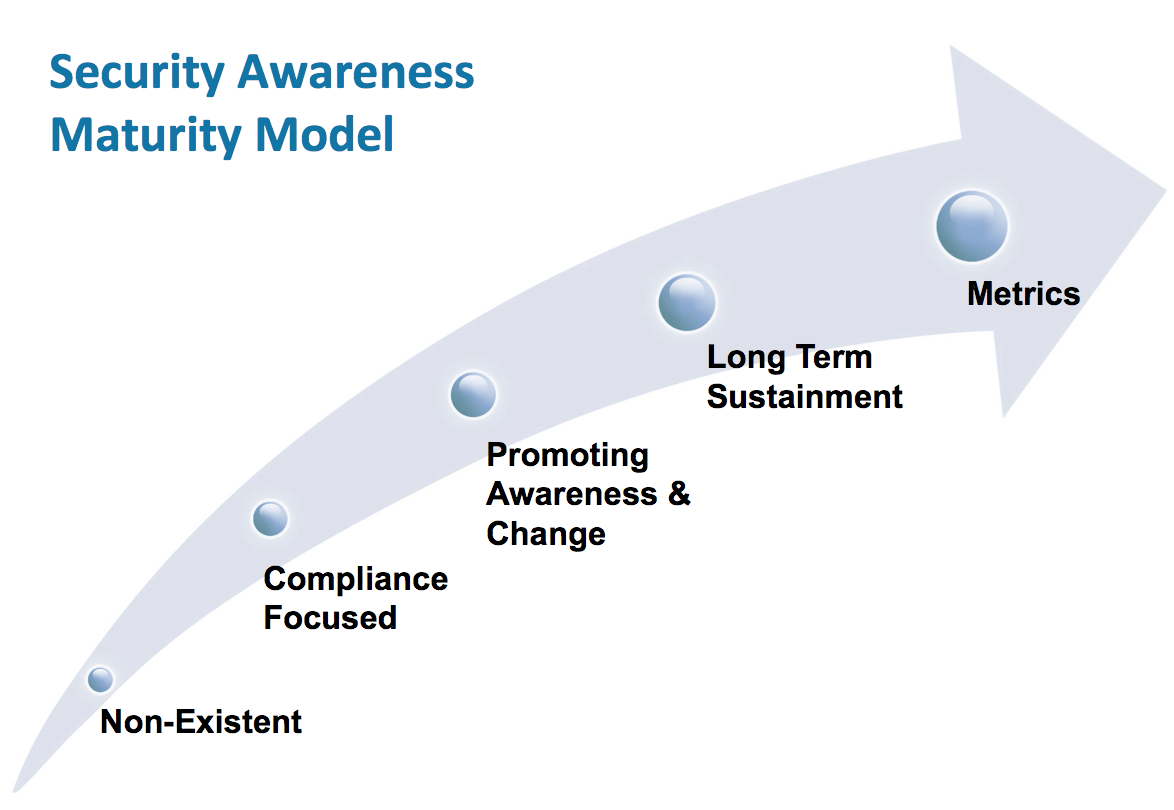
Source: SANS maturity model
Some of the other maturity models are very complex and drill down much further than a few steps or some generalities like the SANS one does. Unless you have mastered some of the smaller ones, though, there isn’t much use in digging deeper. Start somewhere is what is important, as always. How do you eat an elephant was all the way back in episode 4. That thought still hasn’t changed.
Maturity of risk management plans
To get started just ask questions. The process means asking hard questions, though, and providing honest answers. Audit scripts does a 5 questions list for a wide variety of security program elements that some may find helpful. The specific risks you address should be evaluated in some maturity model.
Let’s start with just checking the maturity of your security risk analysis (SRA) plans. To do a proper SRA there should be a list of threats and vulnerabilities. Then, you identify the likelihood and impact to determine the risk you believe they mean to your organization.
When Kardon does a security risk analysis we add a series of questions that ask what is your general plan for those threats and vulnerabilities. Finally, we ask how well are you doing with the plans you identified. Originally, we provided a matrix for making those decisions.
Turns out that was more like parents having to identify problems with their kids – you usually give them the benefit of the doubt. But, when you drill down and ask specific questions the answers change a good bit. We now ask specific maturity questions that automatically calculate a maturity score. Results are dramatically different. Math is so much easier to deal with on these things.
We took the approach that any implementation would require three elements, at a minimum: Training, Documentation, Incident Response Plan prepared. We ask where you stand with each of these elements in addressing a specific risk. Then, math determines your overall level of maturity.
Our maturity levels include:
-
- Chaotic – 0
- Informal – 1
- Reactive – 2
- Stable – 3
- Proactive – 4
- Optimized for continuous improvement – 5
For example, consider a ransomware attack threat, it should be considered a High risk for any healthcare organization. If you answered the element questions as follows:
| Element | Answer |
| Training | Undocumented or no training |
| Documentation | No written policies, procedures, documentation |
| Incident Response | Incident response team concept never discussed |
The maturity level of your program’s ability to deal with that risk is chaotic at best based on those answers. The bare minimum you should be at, in our opinion, for all your High Risk items is Stable. That means the answers would be at least:
| Element | Answer |
| Training | Documented training for staff is comprehensive |
| Documentation | Written policies, procedures, plans, documentation exists and includes proof of regular reviews, and necessary BAAs in place |
| Incident Response | Team has been assigned and working to determine roles and responsibilities consistently |
Ultimately, you would want to be at a Proactive level. However, many organizations are still in the Chaotic level so jumping from 0 to 4 is a big leap. Make progress. It isn’t going to get easier the longer you wait.
Maturity of the organization
Those examples are where we are looking directly at a specific risk and not the organization as a whole. Back in 2014 Enterprise Strategy Group released a matrix that looked at the organization as a whole where cybersecurity is concerned. It says there are three types of organizations: Basic, Progressing, and Advanced. They also look at different categories to define where you stand in each area. Philosophy, People, Process, and Technology.
I think the classification can often be made without anything more than the Philosophy for many organizations. If it doesn’t start from the top then you know it isn’t going to be secure at the bottom. The three Philosophy options are drive the rest of the maturity model. Is cybersecurity a “necessary evil”, something that must be integrated into the business, or part of the culture.
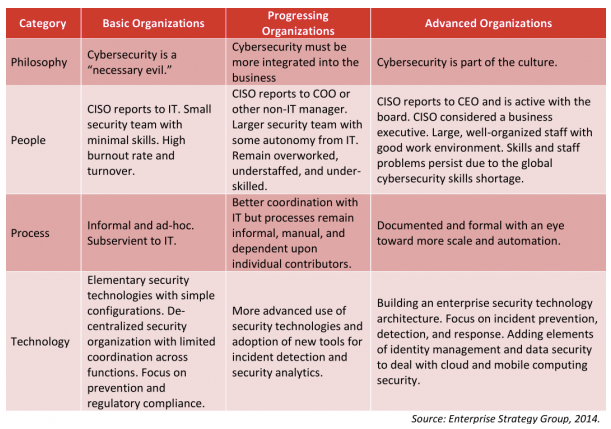
Peter Drucker promoted the concept of “What gets measured gets managed.” Drucker also said that “Management is doing things right; leadership is doing the right things.” Just doing things that aren’t contributing to the growth and effectiveness of your privacy and security program isn’t helpful. You need to see that you are continuing to do things that move you forward and prepare you for the next threat you face. Maturity isn’t a place it is a process that never ends no matter whether it people, processes, or systems.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!


