 As is our custom, each year we have a halloween-themed episode. This year we are thrilled to bring you several very real Tales From The Dark Side Of HIPAA. Thanks to our friend, Jack Rhysider from DarkNet Diaries for recording our haunting lead-in!
As is our custom, each year we have a halloween-themed episode. This year we are thrilled to bring you several very real Tales From The Dark Side Of HIPAA. Thanks to our friend, Jack Rhysider from DarkNet Diaries for recording our haunting lead-in!
In this episode:
Tales From The Dark Side Of HIPAA – Ep 227
The HIPAA Boot Camp
Final 2019 Session
Nov 5, 6, 7
Tucker, GA
For info go to TheHIPAABootCamp.com
[button link=”https://helpmewithhipaa.com/hbc” type=”big” center=”yes” newwindow=”yes”] Registration Form[/button]
Share Help Me With HIPAA with one person this week!
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
Tales From The Dark Side Of HIPAA
We see things and hear things on a frequent basis that just make us cringe and immediately share it with each other to make sure we don’t miss the opportunity to cringe and evaluate the information together. Each of our Tales from the Dark Side of HIPAA share something that happened behind the scenes that most people don’t realize is really going on out there with the people they trust to watch after them and their business.
Tales from the Dark Side of HIPAA #1: Actual post in a discussion board by an MSP
Below is the actual text from the post David found in the discussion board because someone tagged him in the discussion that made him bring it to our tales from the dark side of HIPAA.
Hippa Compliant
Can be accessed remotely from a separate office.
Can limit access to files for different employees/groups. (I.E the front desk doesn’t need access to company ownership files)
I’ve suggested a setting up a server for files & AD or a NAS but the kicker is they only have about 10GB of data. Feels like I’m overselling and there’s a better solution?<span class="su-quote-cite">MSP Owner</span>
You know that we are horrified by the repeated misspelling of HIPAA that someone will always claim as a typo and not an indication right away that they don’t know what HIPAA requires in detail because they can’t spell it.
The level of confidence this person seems to have with their advice concerning HIPAA requirements should be very scary warning sign to all of you who assume your IT provider understands HIPAA because they seem to know it so well. This person does not know the HIPAA of which they speak in the manner of which they believe themselves to be an expert. Let’s count the ways this single post scared us about the posters lack of knowledge of HIPAA.
- Google Drive under G Suite can be used in a HIPAA compliant manner and is done so by many large and small organizations. Just because you don’t know that can be done alone is a problem for us but even more so for your clients because you imply that whomever set it up didn’t know HIPAA properly either. While that may be possible if they didn’t set up the BAA you clearly don’t understand that part either.
- If you do use G Suite you should also set up a G Suite backup solution to address things like staff deleting files and folders they shouldn’t but there is also a history that could have possibly saved the day that you don’t seem to know about because you don’t mention checking it.
- If they aren’t using G Suite with a BAA to store the data on Drive in the first place, then you have a data breach on your hands which should be your number one concern which you should be dealing with properly before giving them a quote. Since it isn’t mentioned at all we will do our best to let this one go because it could cause us to scream and run from the safety of our house into the scary shed with the chainsaws!
- More importantly, they should also have used G Suite security settings to control access for people with the ability to delete things among the other access settings that should be in place under HIPAA. This alone is never mentioned as a concern which may be simply overlooked and assumed by the audience but why do you add it as a requirement as if there isn’t one within G Suite?
- The requirements list for the replacement solution you are convinced that you must provide to them includes items that also give us the heebeegeebees.
-
-
- “HIPPA compliant solution” is not a thing all by itself and if you didn’t seem so uneducated about HIPAA requirements we would let this slide because we would assume you know what that really means when you say it. Due to all the other incorrect implications of this post we must also assume this person believes there is really such a thing as just picking up a HIPAA compliant solution and being ready to roll.
- When the requirement is “can be accessed remotely from a separate office” that tells me there are multiple office and remote access from home or mobile sites which means we must worry about remote access methods not just that it can be done. We may give them a pass here but any time I would include this kind of requirement the word securely would be included in the phrase.
- The final requirement is that the solution must limit access to files and folders for different employees/groups which is a very specific and important requirement of a “HIPPA compliant solution”! That made our skin crawl especially when you add to it that there is no mention of using G Suite security in the first place so there is a concern it will be properly secured even when it does finally happen.
-
-
- The final point says that the MSP has suggested setting up a server with Active Directory to store files or a Network Access Storage device but they don’t want to oversell to the client if there is a better solution for their small 10G of storage needed. With this question added we do appreciate the MSP for taking the time to make the post because it does appear that they do really want to do what is best for the client but their lack of understanding is preventing them from doing the right thing and they just don’t know it. What is terrifying for us is that in so many cases we find that the MSPs come in and just tell the client you need a server with AD and a NAS and Office 365 or you will not be compliant with HIPAA which is absolutely NOT true.
This tale from the dark side of HIPAA is to share with you all that there are MSPs out there that really do not fully understand HIPAA requirements yet they come across to someone who understands little about technology and HIPAA that they are wizards and can do it all for you. They can not and the less they know the worse it can be when the mistakes they make creates a carcass that comes floating to the surface which will be your problem.
Tales from the Dark Side of HIPAA #2: MSP Ghosting
That carcass brings us to our scariest tale from the dark side of HIPAA today because this one left us all with no words to share just saying wow over and over again. If you have a business today you should listen to this campfire story because it is very, very real and very, very scary for all the parties involved. Unfortunately, we can also tell you right now that it is not the only story along these lines that we had to pick from out there.
Here is another story but this one starts with dozens of dental clinics in Oregon and Washington just doing their work on July 3, 2019 which, as we all know that is before a holiday in the US, and those days before a major holiday are also the day that many tales from the dark side of HIPAA begin. Imagine just going about your business trying to get to the end of the work day to start your holiday events when all of your systems start slowing way down and not responding when you are trying to do things until finally you can do nothing. On the screen you soon see a message we all know to mean you have been hit with a major ransomware attack locking your access to all of your patient records as well as other business records.
As everyone tends to do in cases like these you frantically start calling your IT support line and leaving messages but instead of getting any response from IT you get crickets, nothing, not even an email, text message, voice mail, just nothing. As one of the office coordinators interviewed for the article offers up a very scary recount of the response from their MSP had when all of their clients started calling in the panic that a ransomware attack creates.
Portland-based PM Consultants Inc. was the same MSP that took care of everything for all of the impacted dental offices in the area which were hit at the same time. It is pretty obvious to us immediately that the MSP was hit by an attack on the MSP infrastructure that they use to access and support all of the systems and servers at their client sites because this has been going on for a year now. We will get into that a little bit more in a minute.
The problem was this MSP who supported all of these office could not handle the crisis they were dealing with across all of their clients because they were totally unprepared for the situation. They appeared to be completely blindsided by the attack since they never did reply to their customers who were all clearly up an unsanitary tributary without adequate means of propulsion. In fact, according to the Propublica article which had the best information about the case, they simply sent a Dear John email to all of their clients who were in this horrible position because of their trust in PM Consultants.
But wait, there is more, way worse detail to share in this story because not only did they not respond to the clients with anything other than that email a week later but they also sent another one on July 22, 2019 make note that this all just started on July 3rd. This email explained they were shutting down their business effective immediately and said it was “in part due to this devastating event.” Let me tell you they didn’t just shut down a little bit the company was run by a couple with one or two techs they employed and they just disappeared completely. The domain name is shut down for email, no website, the phone doesn’t work and the owners don’t return messages left on their mobile phones. BAM!
The situation is likely STILL an ongoing nightmare for those dental offices in the area with little or no ability to recover their businesses with help from the people they counted on to take care of their technology. Unfortunately, my guess is that none of the dental offices vetted the real understanding of HIPAA the MSP company had and insisted that there be a ransomware incident response plan for their office that included details of how the MSP would respond to a nightmare situation like the one that happened.
If that story doesn’t scare you into requesting a meeting with your MSP the details in our last tales from the dark side of HIPAA will do it or you may end up just like some of these poor folks in the future.
Tales from the Dark Side of HIPAA #3: There are many more
We have mentioned this kind of MSP attack before because since the end of 2018, the FBI has been warning MSPs that they were under attack from China trying to use their tools as an easy gateway to a lot of ransom attacks at the same time.
In fact we have talked about it happening in multiple cases over several episodes as just a discussion but never focused on it but most notably the latest one we mentioned included the attack on Percsoft and DDS Safe hitting around 400 dental practices in the Wisconsin area as well as other states. These offices were certainly frustrated with the vendors slow response times but they didn’t ghost them they at least kept working in order to bring them back to life after a similar attack that was done through the vendor systems to their client systems. The story we have heard is that they paid the ransom to get their clients back up and running but it still took days if not weeks to resolve for all clients.
A new one was just announced coming out of Louisiana yesterday that I am sure we will hear much more about it especially since the first article I have seen from a pediatrics group. They interviewed the administrator who says it was their IT company that was hit and that IT company also paid the ransom to get their clients up and running.
We understand paying the ransom is the fastest way to get back assuming that you only pay once and the decryption routine actually works when you run it. All of us also have to understand that each time they pay there will be another attack on an MSP which will continue until someone stops paying. We are also hearing that is what happened with the 22 towns in Texas that were all hit on the holiday weekend through their IT company. The cities refused to pay up but who knows how the IT company brought them back up.
All of this news really comes to a head when you think back to our first story and our concerns that the IT vendors don’t really understand what you need for HIPAA requirements. Do you think they really understand what they should be doing for their own privacy and security plans so that they are protected from these attacks and prepared to respond to them?
Our concerns about this topic are being proven, unfortunately, with all of this news coming out each week or every couple of weeks where there is another case even. David reviewed a new report (2019 Global MSP Benchmark Report) from a company called IT Glue which is used by a great number of MSPs who were surveyed for this benchmark report on the state of MSPs companies for 2019. The survey results included over 700 MSPs from 23 countries and the stats show that 2/3 of those are in the US so it is a good indicator of US companies in the numbers which tell us a lot of interesting things but something is very striking that jumped out at David while reading the report.
As we know from our Ponemon reports healthcare as a business vertical really only exists in the US in other countries it usually falls within the public sector somewhere. According to the summary numbers 1/3 of the respondents specialized in a vertical and most of those were in healthcare. Now, we have set the stage for the part that really is terrifying based on these stories we just told you concerning MSPs ability to protect you. Of those surveyed when asked to rank the metrics they felt were important on a scale of 1 to 5 with 5 being most important Compliance received a 2.31 score which went along with Human Resources scoring a 2.2. They don’t worry about compliance in their own business which explains a lot of the problems we are seeing in the horrifying tales!
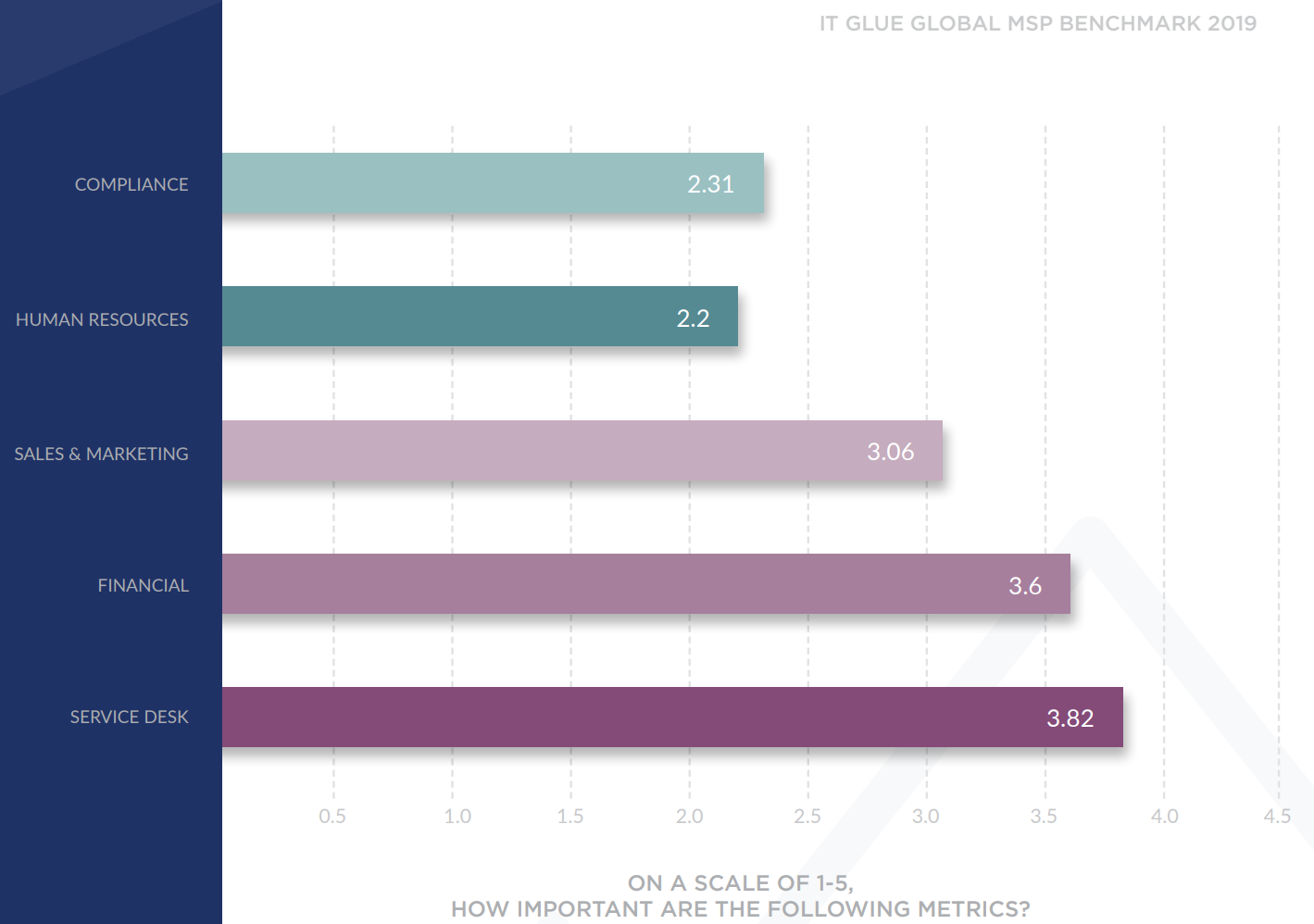
The next time your MSP or IT company is preaching to you about compliance that you should be doing muster your best monster voice and ask what are THEY doing to manage their own compliance. While it is a valid question to ask based on these stories and survey results it is your business that will suffer if they don’t have a plan to deal with these new issues. You have every right to demand they show you what they are doing to plan for these situations and staying on top of the changing threat environment.
It could be that some of the companies were really prepared but something went way wrong in the plan that threw them into crisis. I know we constantly worry that it will happen to us which is why we are always checking and asking and documenting and comparing and getting training ourselves. Just make sure your people that have all of your data in their hands are doing the same thing or you could be the ones featured in next year’s horror story episode! BWAHHHHHH
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!


