
Protecting your company’s data is no longer optional. With so many changes in how people work today and where they are working from, keeping a low profile when it comes to protecting data won’t cut it anymore. Today, we review a recent report released by Shred-it, a secure information destruction company, called Data Protection Report 2021.
In this episode:
Taking the Team Approach to Privacy and Security – Ep 333
Today’s Episode is brought to you by:
Kardon
and
HIPAA for MSPs with Security First IT
Subscribe on Apple Podcast. Share us on Social Media. Rate us wherever you find the opportunity.
Upcoming Events:
The HIPAA Boot Camp Virtual Edition Feb 22-24, 2022
Sign up now.
The Privacy and Security Boot Camp
3.5 day In Person Event
Sep 12, 13, 14 and 15
More details coming soon…
Learn about offerings from the Kardon Club
and HIPAA for MSPs!
Share Help Me With HIPAA with one person this week!
Thanks to our donors. We appreciate your support!
If you would like to donate to the cause you can do that at HelpMeWithHIPAA.com
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
If you see a couple of numbers on the left side you can click that and go directly to that part of the audio. Get the best of both worlds from the show notes to the audio and back!
HIPAA Say What!?!
[11:44] NJ SAG announced another HIPAA case settlement on a case going back to 2016. Acting AG Bruck Reaches Settlement with Two Printing Companies over Improper Disclosures of Protected Health Information – New Jersey Office of Attorney GeneralOk, let me just say this up front: After reading the court document on this case, this doesn’t make sense to us. I am still confused. So, go read the case yourself and see if you can follow it.
We have two companies and a customer involved in this case:
Strategic Content Imaging, LLC (“SCI”) is a Secaucus, New Jersey-based company that provides digital print, finishing, and fulfillment services to businesses;
“Customer” shall refer to a leading New Jersey-based managed healthcare organization with whom CMI executed a BAA and for whom CMI agreed to provide mailing, fulfillment, and printing services, including the printing and mailing of EOB statements.
Now this is the confusing part:
Huh? It’s like they think there can only be a CE to BA relationship and not a BA to BA relationship. Ok so let’s move on. The brief says:
Corrective actions:
Do what?!!?! Even if they could get HITRUST certified in 120 days, it wouldn’t have prevented this situation from happening.
Again… huh? Once again, this would not have changed what happened. There is so much wrong with this whole case. You’ll have to listen to the podcast to hear our confusion and frustration in understanding it.
Taking the Team Approach to Privacy and Security
[26:08] Shred-it, the document destruction company, released their annual data protection report recently – Data Protection Report 2021.The title “No Longer Optional: Invest in Data and Information Security Now or Pay Later”—reveals gaps and opportunities for both physical and digital data protection.”
The focus of the company is shredding, but the report has a lot of very good information about protecting all information in your company. This report is not just a healthcare focused report. It includes data from five industustries:
- Healthcare
- Finances
- Professional Services
- Insurance
- Real Estate
Respondents tracked also included C-level executives, consumers, and SMB.
The information in this report is really helpful and covers a wide range of stats people in our business can use for decision making assistance. Believe it or not, we don’t just say things because we think it is a good idea. We have data to explain why we believe in our recommendations.
[28:34] Keep in mind that this study was done for Canadian businesses as well as the US. But, check out these stats:
Here are a few interesting quotes from the study:
When the estimated cost of a data breach is $13,786 per day, it is imperative that businesses have an incident response plan and remediate quickly.
Approximately 3 in 10 consumers (U.S. 32% and Canada 25%) will share their experience with others and nearly 1 in 4 (U.S. 23% and Canada 20%) will stop doing business with the company responsible for the breach.
The stat in this next chart is alarming… the C-suite folks report that 53% of data breaches were caused by malicious insiders. This number seems to be growing.
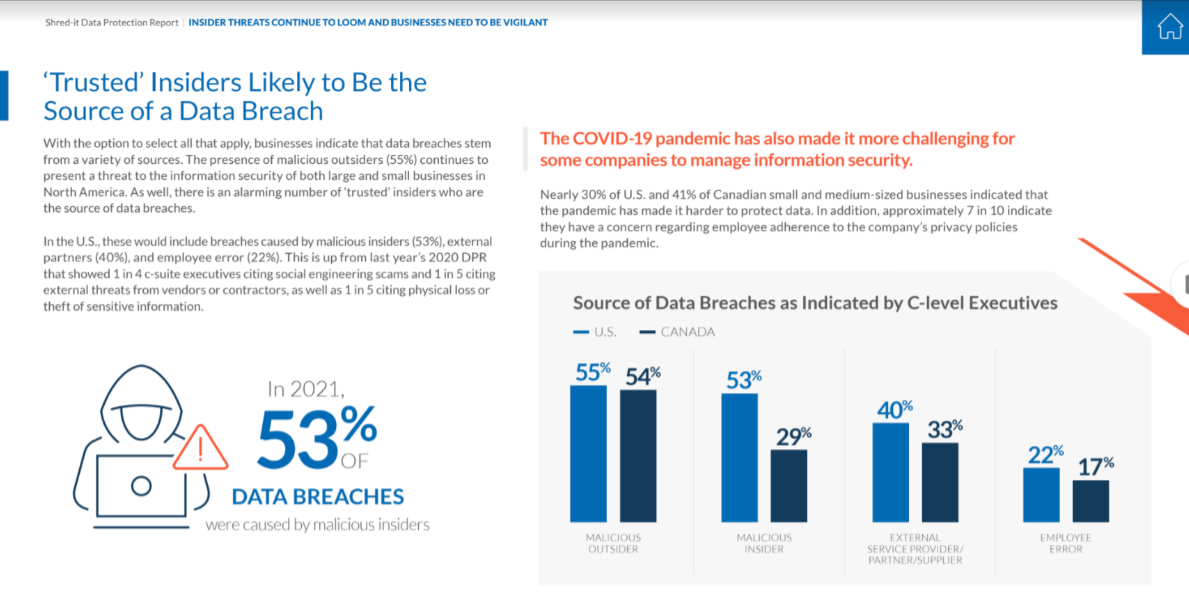
So, what can we do to fix it?

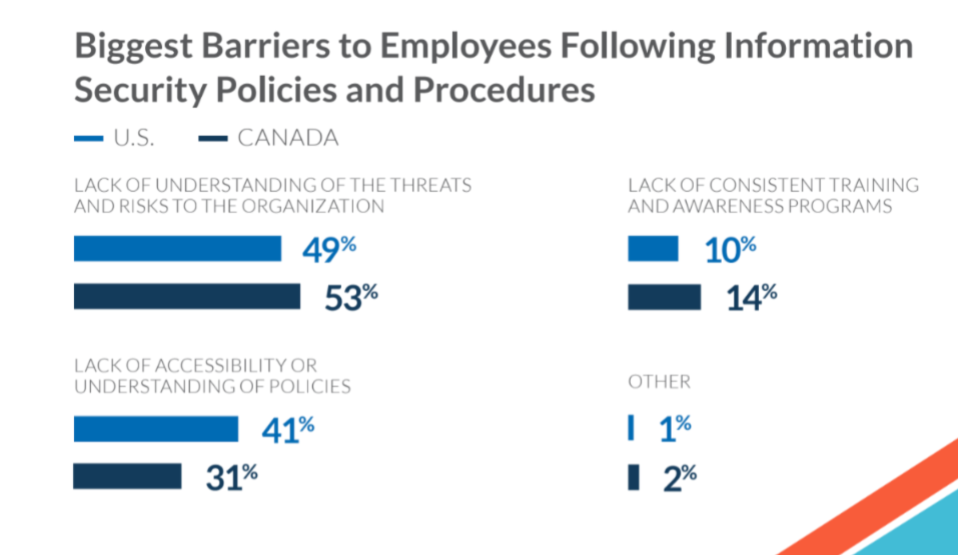
The problem is that business leaders tend to be the worst at understanding or even paying attention to studies or presentations regarding threats to their company or its data.
There were also some specific findings from healthcare included in the report:

The above chart looks pretty good when you see that 75% say that information security is very important to their company. But, check out the other stats in the chart. Not so good. When you say it’s very important but you aren’t doing what would actually be involved in taking security seriously, then that 75% doesn’t seem accurate, huh? If you can’t prove you are taking it seriously, you aren’t.
Excellent Summary with 7 very good points included
[39:56] There are a couple sections in the Data Protection Report that I thought were great. First there is the “Understand your data” section. So, that’s a good place to start. But, then there is the “Prepare to Act” section. This section basically says “policies are not enough” and “protecting data is a team sport.” They came up with the 7 recommendations that can help create a strong line of defense to prevent a data breach:A business’s best line of defense starts inside. Equipping employees with the proper tools and knowledge will empower them to become ambassadors for information security—encouraging others to do the same. Companies should also ensure they know what vendors are doing to keep their information safe. To create a strong line of defense to prevent a data breach, businesses should:
Create a security-minded corporate culture for data protection best practices. Data is the lifeblood of any organization and protecting it is a team sport. It’s important that employees understand the full picture impact of a breach. Not only does a breach impact day-to-day business, but it could impact their job security.
Well knock me down and steal my teeth! Double D’s done told you that!
Privacy and security is a team sport. That is why the Kardon Club logo and branding is modeled after a Football/Soccer Club. Yes, you are a member of the club just the same as a member of the team. We have made these points many times and in many ways. Everyone must be part of the protection scheme today. No team wins without an involved leadership, a front office managing things, coaching and support staff, practice teams, and qualified reserves.
Businesses should implement policies to address the information security of the enterprise, the privacy of consumers’ data, regulatory security guidelines (such as those for HIPAA in healthcare and the Gramm-Leach-Bliley Act in financial services), and physical security for data in all forms—including electronic and printed documents. But, for a policy to be effective, businesses should provide training programs to help employees put the information into practice to ensure understanding and adherence.
You know we have covered this before, too. If you don’t get the message to the team, it doesn’t matter how many plays you write up. Each person needs to understand their position and their importance. The only way they do that is seeing the big picture as well as understanding their role in that big picture. Your team can be crushing it on the field, but if the people who are supposed to make sure they stay hydrated are just watching the game and not doing their part, your team will not be crushing it for long!
Businesses should institute policies to ensure employees understand the expectation around document handling and retention. Policies, such as a clean desk, shred-it-all, and remote work will take the guesswork out of secure document handling and reduce the risk of human error. The policy must clearly state the expectations and the steps that will be taken when violations occur.
If your plays aren’t working it may not be because your team is bad, it may be the plays are bad. Evaluate what is working and what is not working. If you update your plays so that each member of your team can do their jobs effectively and efficiently utilizing their strengths, you are much more likely to be successful.
[48:04]
Policies are only just the beginning. Employees should be trained to ensure they understand and can implement the expectations outlined in the policy. Businesses can employ a variety of training initiatives such as phishing simulations to encourage employees to be vigilant and promote adherence. Incentives can also be used to reward employees that report security dangers. The enthusiasm that results pushes data protection programs and initiatives forward.
Guess what!?! Humans usually need to be motivated to do things consistently. Especially if those things require commitment and consistently following a strict regimen. There are many ways to motivate a team so don’t think that what worked with one group will work equally as well with another. You must find what matters for each group. Then, train towards that goal. Positive reinforcement works many times better than negative reinforcement.
Consider implementing two-factor authentication for all users when accessing critical systems and applications. Also consider a zero-trust approach to network access requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and validated for security configuration prior to being granted access to applications and data.
We just talked with Ray Ribble of SPHER (Do you audit your EHR logs? – Ep 329) about the importance of monitoring for insider threats. You must accept it is an issue and address it with policies, procedures, training, and monitoring. This is definitely something we have covered repeatedly. The “one bad apple spoils the whole bunch” proverb didn’t come out of nowhere. That statement goes back centuries. It is funny (but not) when people use it incorrectly. To simply say there are a few bad apples in the group as an excuse for bad behavior to say there are only a few problems not a big one misses the mark. If you have a few bad apples your whole barrel is going to rot until there are no bad apples. You can’t excuse them and expect the rot to stop. All it takes is one bad apple and you are in serious trouble. Period. You always hear about losing teams having “problems in the locker room” or “communications challenges,” but you never hear that about a winning team.
Demonstrate competence in your response to any data breach by preparing yourself with an incident response plan. Make sure that you have a mitigation and communications plan that will enable you to move quickly. Consumers rapidly lose trust in brands and organizations that do not alert them of a security breach involving their personal data in a timely manner. Provide customers with transparency about what happened and how the company is taking steps to prevent a data breach from happening in the future.
Yes, we are sensing a theme here too! Without an incident response plan, you are going to be making major mistakes that can impact your business and potentially endanger patients. The more we learn, the more we understand these plans must be more than just a couple of folks figuring out what to do when something happens. Build the relationships you will need and get your contacts documented and tasks assigned in advance. The team must have reserves and backups for the backups. The front office and leadership must be prepared to bring in experienced veterans when your rookies need guidance.
These services can help cover the cost of legal services and advice as well as crisis management services. Additionally, they can inform and prepare a businesses’ response to a data breach including notification of affected parties (business customers or individuals whose data was accessed or acquired during the breach).
BAM! We definitely said this before. We are in business because we understand that people need the help we offer. Just like a team invests in trainers, doctors, lawyers, PR firms, etc , you must do the same. Get the right help in place when you need it and have insurance plans in place because you don’t want to worry about getting that help when you need it.
If you haven’t already, listen to our podcast episode Cyber Liability Trends with John Miller – Ep 288 to hear more about cybersecurity insurance and what it will and won’t cover and why.
The Shred-it Data Protection Report 2021 is an excellent report for people to have to reference when you are making business decisions, when you need to talk to leadership, when you’re trying to figure out where you belong in the big picture. Make the dream work with teamwork. Get everybody involved.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
HIPAA is not about compliance,
it’s about patient care.TM
Special thanks to our sponsors Security First IT and Kardon.


