 This is not another episode about preventing and responding to the NotPetya ransomware. There are countless articles about those topics. We are discussing the bigger picture today. In this episode, NotPetya, Windows, and Ransomware, we discuss what happened in the case but also what does all of this really mean in the big picture of cyber attacks. If you don’t stay proactive in evaluating what the criminals may do next then you don’t have a chance of being anything but reactive.
This is not another episode about preventing and responding to the NotPetya ransomware. There are countless articles about those topics. We are discussing the bigger picture today. In this episode, NotPetya, Windows, and Ransomware, we discuss what happened in the case but also what does all of this really mean in the big picture of cyber attacks. If you don’t stay proactive in evaluating what the criminals may do next then you don’t have a chance of being anything but reactive.
In light of these recent global attacks, we have many questions. Are we experiencing a shift in the criminal’s intentions or are they just bumbling around with new toys? If is it no longer just about taking our money then what is really about? If you haven’t cared about protecting your data so far, how about protecting your data from becoming a pawn in the latest cyberwarfare battle?
In this episode:
Episode Title
Where to meet us [3:05]
The Atlanta Association of Legal Administrators – July 19, 2017, Atlanta, GA
The HIPAA Boot Camp – August 24 & 25 [3:47]
The Unconvention Sept 16 & 17 in DC – David will be there
North Metro MGMA – Oct 17, 2017, Kennesaw, GA
Georgia Association of Orthopedic Executives, Nov 10, 2017
Topic for today: NotPetya, Windows, and Ransomware [6:05]
Today’s topic
NotPetya, Windows, and Ransomware
With a topic like this one you can tell we may be all over the place but we do have a point in here. This latest round of ransomware called NotPetya or whatever means the Windows needs to get better and this as do users.
What Does The New Attack NotPetya Mean
We are getting into new territory now. There is so much between WannaCry and NotPetya that touches new ways for using these tools. What we have come to expect from standard ransomware attacks that are all about money is not part of these cases.
Chaos and damage are the standards set by this latest round. It is a very serious concern that we may be seeing some sort of military or activists use. Possibly even criminals using random infections of strangers around the world to distract the world from their real intentions.
Petya Is Where We Started This Time
Petya is Russian for Little Peter. Started in Russia. But this now seems to be a bundle of this software along with even more tools. It is much more sophisticated.
NotPetya
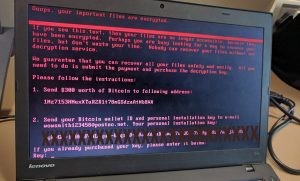 This one is nasty. If you tried to pay you just give criminals money. There is no way to get a decryption key from them. The single email address it uses was shut down.
This one is nasty. If you tried to pay you just give criminals money. There is no way to get a decryption key from them. The single email address it uses was shut down.
This infection does a little work, then waits for a reboot to actually encrypt the master boot record. Basically, that means it makes the hard drive locked out completely. No decryption key will be developed unless there is a problem found in the logic for it.
But…. here is where it gets scary…..
One machine is enough
It looks for any kind of credentials it can harvest from the system memory. Not the person who is logged in. But, more importantly, it is looking for admin credentials. It is a sophisticated approach that other malware has used. Once it gets the credentials it can even infect machines with the patches in place and continue to spread across the network.
>Scott says systems at his unnamed firm were mostly patched against MS17-01. Even so, he says it appears that one PC initially became infected, and the virus extracted credentials from this system before propagating across the network.
MeDoc Software Company update spread it
Security researchers say MeDoc may be the “patient zero” – the first victim to be infected with the malware.
The operational security expert is known as the Grugq notes in a blog post: “Everyone that does business requiring them to pay taxes in Ukraine has to use MeDoc (one of only two approved accounting software packages).” So an attack launched from MeDoc would hit not only Ukraine’s government but many foreign investors and companies. It seems that Maersk was also using MeDoc.”
What is it really about
Clearly, money isn’t the primary motive. What can the motive be then if not something more nefarious? With WannaCry it seemed that the criminals behind it were not prepared at all for the rapid proliferation of their tool.
This time, though, there is no real attempt to get money. The goal isn’t obvious at this time but clearly, they intended for it to spread and wreak havoc.
With all of this activity and more tools being dumped from NSA and CIA hacking scandals, we are just getting started. We can no longer assume that the criminals have the same intent with their malware. It can really be done just as a distraction for something much more nefarious or dangerous to be taking place.
Coming Soon: Windows 10 Anti-ransomware Features
Microsoft announced new features to be included in the fall update. The problem is it is part of Windows Defender which gets turned off in most business systems. In our discussion, we agree there is some concern about the implementation actually being helpful for anyone other than the most basic home user.
I know many people who say they will just go back to paper charts because this is too hard, too expensive, or too chaotic for them. I think that is a great idea to protect yourself from cyber threats if you could do it. For the vast majority of the world, though, that ship has sailed some time a few years ago. If you don’t have the ability to connect and share information electronically it is possible you could be considered backward, outdated, irrelevant, third-world, etc.
Yes, many people will say they don’t care about all of that in a conversation. But, take away all their electronics and see how they handle it for a week. No cheating having someone else do it for you because you don’t want them to have it either. No smartphone, no tablet, no laptop, no desktop computer at your fingertips at all. OK, maybe a flip phone but still no cheating by having someone else Google everything for you.
Please remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
Remember, HIPAA is not about compliance, it’s about patient care.


