
Honeypots are an important tool in the cybersecurity arsenal. They can be used to observe how attackers work and what their activities, intentions and strategies are. This information can help organizations better understand and defend against cyber attacks.
In this episode:
Honeypots Get Quick Attention – Ep 340
Today’s Episode is brought to you by:
Kardon
and
HIPAA for MSPs with Security First IT
Subscribe on Apple Podcast. Share us on Social Media. Rate us wherever you find the opportunity.
The Privacy and Security Boot Camp
3.5 day In Person Event
Sep 12, 13, 14 and 15
More details coming soon…
Learn about offerings from the Kardon Club
and HIPAA for MSPs!
Great idea! Share Help Me With HIPAA with one person this week!
Thanks to our donors. We appreciate your support!
If you would like to donate to the cause you can do that at HelpMeWithHIPAA.com
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
If you see a couple of numbers on the left side you can click that and go directly to that part of the audio. Get the best of both worlds from the show notes to the audio and back!
HIPAA Say What!?!
[02:56] This is a sho ‘nuff HIPAA say what!?! I saw this on Twitter and was just shaking my head. Really dude!? I hate to even give this air time, but if I don’t somebody will try to convince folks that it is true.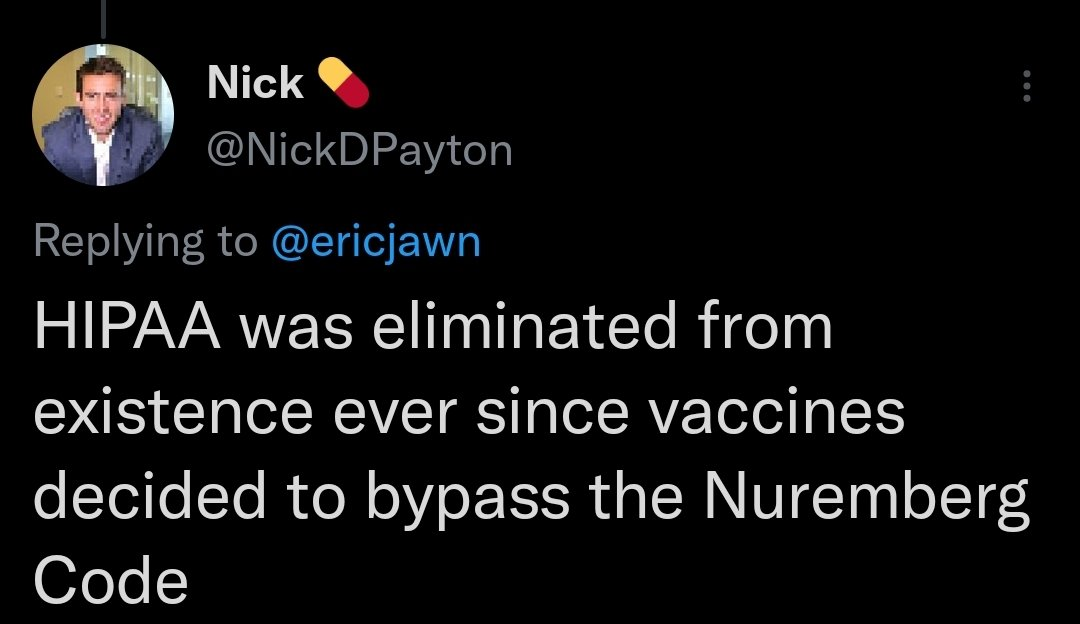
So, just to be clear, Nick is WRONG! HIPAA has not been eliminated. It is still a thing. I bring it up so you will know this is out there in the social media machine. Please don’t be someone who promotes this kind of false information.
Honeypots Get Quick Attention
[09:10] What is a honeypot, you ask? They are systems that are deliberately left vulnerable to attack, in order to gain information about the attacker. The point of a honeypot is to set up a controlled area where software resides to entice people to try to snoop or even attempt a malicious attack.Researchers and cybersecurity folks create honeypots to collect data to see how quickly vulnerable systems are found, how hackers are finding them, what they are looking for and what kind of attacks they might try to launch.
[15:08] Palo Alto Networks researchers did a study where they deployed 320 honeypots across the world made up of multiple misconfigured instances of common cloud services, including remote desktop protocol (RDP), secure shell protocol (SSH), server message block (SMB) and Postgres databases. There were accounts configured to have default or weak passwords — exactly the sort of things that cyber criminals are looking for when trying to breach networks.Threat actors find and compromise exposed services in 24 hours
These researchers wanted to test cloud security. They were shocked by what they found
Some of the sites were compromised in minutes while 80% of the 320 honeypots were compromised within 24 hours. All of them had been compromised within a week. If this was your business that left a system exposed on the internet, you have roughly one week to figure it out and secure it before it could be potentially found. That’s not a comforting feeling at all.
Then, once the honeypot was found, the hackers spent a lot of time trying to figure out what they could do with the exposed network. Each of the SSH honeypots (SSH is a way someone can talk to a computer or connect to it to run commands) were compromised 26 times a day on average. The most attacked honeypot was compromised a total of 169 times in just a single day. Also, one attacker compromised 96% of the 80 Postgres (which is a database tool) honeypots within a single 90-second period. The RDP protocols were found and attacked as well.
Insecure cloud services are regularly targeted by cybercriminals and can be a huge risk to organizations, too. Hacking groups can target vulnerabilities in cloud services as a way to infiltrate a network to conduct espionage, steal data, or deploy malware without detection.
The speed at which these threats were found is staggering.
There are so many things that hackers can do once they have access to a vulnerable network. They can steal data, plant ransomware, perform extortion tactics, plant other malicious attacks, encrypt devices (including backups), even sell your IP address to other bad actors so they can attack your networks too. There is no magic wand either. Your security teams have to stay on top of things. Just having a firewall isn’t enough. You have to make sure your firewalls and devices are constantly kept up to date on the latest software and firmware versions, logs should be reviewed constantly, scans should run more than just once a year to determine what devices, apps and systems are vulnerable, etc.
[30:40] A recent article I read pointed out that hacker gangs are gaining access to systems and within 30 minutes have already stolen your data and set off their extortion plan or just simply left your system to attack it again another day. You may not even know they are in there unless you are paying attention and see activity in logs.These days, hackers can do so many things once they have compromised a network. They don’t always go after your data or conduct a ransomware attack. They might be selling the IP addresses to your network to other bad actors so they can sell bandwidth to do crypto mining or to manage other ransomware attacks.
Here’s the truth about the crypto miner that comes with Norton Antivirus – The Verge
Attackers Are Selling Their Victims’ Internet Bandwidth
Threatpost recently posted an article, 30 Mins or Less: Rapid Attacks Extort Orgs Without Ransomware, said that one cyber group “…exploits unpatched VPNs and webserver apps to breach systems and carry out quick-hit extortion in less time than it takes to order a pizza.”
This article quoted the NCC Group’s Threat Intelligence saying it:

Don’t forget. Cybercrime and RAAS is a big business. It’s its own industry. And they don’t just advertise their products either. Some ads advertise the data they’ve stolen for sale. Someone could buy it and extort your business all over again.
Act now, folks. Don’t play around with thinking you don’t have anything a hacker wants or you are too small for anyone to attack. And don’t put it off til next year or Q2 or after tax season. The criminals know that’s a typical response too. They could target you as you are working on your year end finances. If they get in and shut you down, you are likely to pay more than you would otherwise.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
HIPAA is not about compliance,
it’s about patient care.TM
Special thanks to our sponsors Security First IT and Kardon.


