 A new report on phishing was recently released titled: Data Breaches, Phishing, or Malware? Understanding the Risks of Stolen Credentials. The report of findings from a study that was done by Google, University of California, Berkeley, and the International Computer Science Institute. It was a year-long study of account hijacking, stolen credentials, phishing and malware attacks. The findings are clear that phishing is a problem in ways we may not have thought before now. In the study, the researchers followed other hacker methods used against email addresses they found on the darknet sites for sale. The search netted 12.4 million addresses that were determined to be potential victims of phishing kits out of the total 1.9 billion usernames and passwords exposed by data breaches. So, it is obvious that this isn’t a tiny study over a short amount of time.
A new report on phishing was recently released titled: Data Breaches, Phishing, or Malware? Understanding the Risks of Stolen Credentials. The report of findings from a study that was done by Google, University of California, Berkeley, and the International Computer Science Institute. It was a year-long study of account hijacking, stolen credentials, phishing and malware attacks. The findings are clear that phishing is a problem in ways we may not have thought before now. In the study, the researchers followed other hacker methods used against email addresses they found on the darknet sites for sale. The search netted 12.4 million addresses that were determined to be potential victims of phishing kits out of the total 1.9 billion usernames and passwords exposed by data breaches. So, it is obvious that this isn’t a tiny study over a short amount of time.
In this episode:
Five Phishing Findings From Google – Ep 132
Where to meet us [1:20]
GSASC/SCASCA Joint Semi-Annual Conference and Trade Show Feb 16, 2018, in ATL
2018 JAWS Society Annual Conference, (a national society of oral and maxillofacial administrators) April 22-25 in Newport Beach, CA
Learn more about our Live HIPAA Boot Camp and request one in your area: www.HelpMeWithHIPAA.com/bootcamp
Want to be part of Help Me With HIPAA? Become a Patreon at www.HelpMeWithHIPAA.com/give
HMWH App now has more features. You can now access a PDF with the show notes ready for your HIPAA training documentation! Find it under the bonus feature in the app for both the Apple and Android versions. It is a little gift box on the [3:06]
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
Listener email about “say her name” episode. [4:36]
The topic for today: Five Phishing Findings From Google [7:57]
Today’s topic
Five Phishing Findings From Google
We came up with 5 points we plucked from the study that we believe are key reasons we should ALL be doing more to prevent phishing attacks. This really isn’t as much about HIPAA but more of a throwback to our episode on building a national culture of cybersecurity earlier in the year.
1 – Phishing is prevalent and it is going after more information on your computer system than just your email and password.
Eighteen percent of phishing kits collect a phone number, while 16 percent collect user-agent data, which comprises various parameters encompassing the operating system in use, versions of software and web browser details, according to the study. That enables attackers to attempt to more closely mimic someone when trying to access an account.
As they gather that data there are many other things they can figure out and then use it against you. It isn’t just about your office email address either. What if you are phished at work but using your personal Gmail account? Across the board, they can see that the hackers will review the email account searching each victim’s email history for financial records and credentials related to third-party services.
Table 8: Additional information stolen by phishing kits and keyloggers. We note that some phishing kits exclusively collect credit card details rather than usernames and passwords.
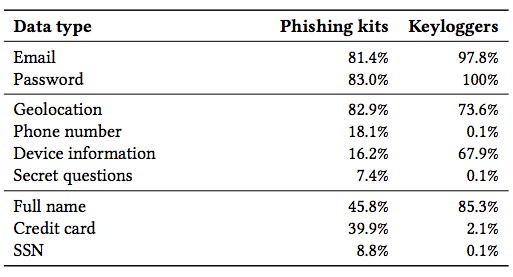
BTW, they identified 4,069 distinct phishing kits in their research. That was several thousand more than the other type of attacks. Phishing kits are “ready-to-deploy” packages for creating and configuring phishing content that also provide built-in support for reporting stolen credentials.
2 – If you fall for phishing you are 400 times more likely to lose your credentials than the average Google user.
We find victims of phishing are 400x more likely to be successfully hijacked compared to a random Google user. In comparison, this rate falls to 10x for data breach victims and roughly 40x for keylogger victims.
Come on man! 400 times more likely to be successfully hijacked. If we can’t get folks better educated on how to properly use their accounts we will never be able to win the battle.
3 – Really! The password thing matters!
If you are using the same passwords over and over once they get one of them they have all of them!
4 – The hacker tools haven’t really changed since mid-2000’s.
We keep falling victim to the same tricks that have been in play for as much as 20 years. Part of that probably has to do with the new users of the internet continuing to be added. But, the majority of the issues are the same ones we address over and over again. It’s the people, people!
5 – You can’t just keep rolling along after a hack like nothing happened.
There must be some changes made to your behavior once it happens.
Even if people realize they’ve been compromised, however, many rarely take action to improve their defenses. “Our own results indicated that less than 3.1 percent who fall victim to hijacking subsequently enable any form of two-factor authentication after recovering their account,” the researchers write in their paper.
How do you combat this stuff? []
- Training – Not some “check it off the list” annual going through the motions junk either. Training has to be regular and repetitive.
- Simulated Testing – know exactly who the problem employees are and what they need training on. Test your staff with phishing campaign.
- 2FA – Two Factor Authentication. Yes, it is an extra step but well worth the protection it provides. Check out the episode we did on 2FA and find a way to set that up.
- Password Managers – One password to rule them all. We like and use LastPass but there are plenty of other options if you don’t like LastPass.
We continue to see HIPAA breach notifications relating to phishing incidents like Wisconsin and Braxton. It is clear these cases will continue happening until we do better than these numbers say we are doing. Phishing hasn’t changed in so long because there is no need for the criminals to do so. Until we do the hackers can continue to use us as pawns in their games for financial gain.
Please remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!


