Every year we review the Ponemon Institute’s Cost of a Data Breach report. It’s always interesting because we learn that it’s not just about the money. We learn what really makes a difference in our privacy and security program, what we can do that can make the biggest positive impact in the overall cost of a data breach and, more importantly, what things make the biggest negative impact.
In this episode:
Cost of a Data Breach 2022 – Ep 375
Today’s Episode is brought to you by:
Kardon
and
HIPAA for MSPs with Security First IT
Subscribe on Apple Podcast. Share us on Social Media. Rate us wherever you find the opportunity.
The Privacy and Security Boot Camp
3.5 day In Person Event
Mar 12, 13, 14 and 15, 2023
PriSecBootCamp.com
Great idea! Share Help Me With HIPAA with one person this week!
Learn about offerings from the Kardon Club
and HIPAA for MSPs!
Thanks to our donors. We appreciate your support!
If you would like to donate to the cause you can do that at HelpMeWithHIPAA.com
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
If you see a couple of numbers on the left side you can click that and go directly to that part of the audio. Get the best of both worlds from the show notes to the audio and back!
HIPAA Say What!?!
[04:10] HHS Announces Melanie Fontes Rainer as Director of the Office for Civil RightsNot sure about the shake up in leadership but at least the post wasn’t open for months. Hopefully, that means some of the stuff that we really need to get done will start moving forward and we’ll get further guidance on recognized security practices, as well as the NPRM about privacy rule changes that have been hanging out there for a while. So, we are looking forward to that and much more.
405(d) Tip of the Week
[06:36] The 405(d) Post Volume XVII – Sep 2022There are some very interesting articles in the newsletter, including Legal Implications of a Cyber-Attack and Cybersecurity Policies for Small Healthcare Organizations.
Cost of a data breach 2022
[07:59] Cost of a Data Breach Report 2022 | IBMCost of Data Breaches Never Sound Good
Now in its 17th year, this research — conducted independently by Ponemon Institute, and sponsored, analyzed and published by IBM Security® — studied 550 organizations impacted by data breaches that occurred between March 2021 and March 2022.
The breaches occurred across 17 countries and regions and in 17 different industries. They conducted more than 3,600 interviews with individuals from organizations that were impacted by the data breaches. Another thing to note is the study looked at breaches sized between 2,200 and 102,000 records.
Let’s take a look at the key findings of this report:
Like Everything Else, The Cost Is Going Up
Yet again reaching an all-time high, the cost of a data breach averaged $4.35M in the 2022 report. This figure represents a 2.6% increase from last year, when the average cost of a breach was $4.24M. The average cost has climbed 12.7% from $3.86M in the 2020 report.
The continuing rise isn’t something that just happened though. There has been a fairly continuous upward trend since 2017. A small dip in 2020 will not be considered anything other than an anomaly because…. 2020.
The cost per record in 2017 was $141 and this report puts it at $164 per record. Interesting that they point out that due to the size of the breaches in the study, they do not believe the use of these by record numbers would be accurate if the number of records is above 102,000. There goes the idea that these numbers are high because they include a bunch of huge breaches.
But wait, there’s more! Those are the global stats. For the 12th year in a row, the US had the highest average costs by far at $9.44M.
And The Winner Is… Healthcare! (Again)
[14:06] The average cost of a data breach for global critical infrastructure organizations studied was $4.82M. That’s $1M more than the average cost for organizations in all other industries. But, we also know that one of those in the US is healthcare. Not exciting news but also not unexpected.For the 12th year in a row… that’s right 12 years in a row, healthcare has secured the #1 spot for the highest breach costs of any industry.
This year average costs hit another record high and increased another $1M, to a whooping $10.10M. That is a 46% increase in just 2 years.
The #2 spot goes to the financial sector, but is nearly half of the cost of healthcare at $5.97M.
Do you have a longtail?
Now that they have years worth of data they have been able to look at long term costs that span out 2 years or more. We often mention how you can’t assume this will be over in a month or two – it can drag out for years. Comparing low regulatory environments vs high ones they noted:
Certainly, that has an impact on the costs for healthcare but what is interesting is how the costs spread out in that comparison. Highly regulated companies spread is at or below the 2022 average until the 2 year mark. Low regulation groups spend almost all of the costs in the first 9 months. Those costs at the longtail in healthcare are not huge penalties like you see in the financial industry. They are corrective action plans and legal fees that pile up, at least IMHO.
Yes Sir, I’ll Have Another!
[18:46] 83% of organizations studied have experienced more than one data breach, and just 17% said this was their first data breach. 60% of organizations studied stated that they increased the price of their services or products because of the data breach.Security With AI & Automated Response Makes An Impact
Breaches at organizations with fully deployed security AI and automation cost $3.05M less than breaches at organizations with no security AI and automation deployed. This 65.2% difference in average breach cost — between $3.15M for fully deployed versus $6.20M for not deployed — represented the largest cost savings in the study.
Companies with fully deployed security AI and automation also experienced on average a 74-day shorter time to identify and contain the breach, known as the breach lifecycle, than those without security AI and automation — 249 days versus 323 days. The use of security AI and automation jumped by nearly one-fifth in two years, from 59% in 2020 to 70% in 2022.
Some Good News… Sorta.
[24:26] Eleven percent of breaches in the study were ransomware attacks, an increase from 2021, when 7.8% of breaches were ransomware, for a growth rate of 41%. The average cost of a ransomware attack went down slightly, from $4.62M in 2021 to $4.54M in 2022. This cost was slightly higher than the overall average total cost of a data breach, $4.35M.Credential Compromise Is Still The Biggest Problem
Use of stolen or compromised credentials remains the most common cause of a data breach. Stolen or compromised credentials were the primary attack vector in 19% of breaches in the 2022 study and also the top attack vector in the 2021 study, having caused 20% of breaches. Breaches caused by stolen or
compromised credentials had an average cost of $4.50M.
Compromised credential breaches also had the longest lifecycle — 243 days to identify the breach, and another 84 days to contain the breach.
Phishing was the second most common cause of a breach at 16% and also the costliest, averaging $4.91M in breach costs. Not sure if they count the phishing attacks that steal credentials as one or both categories.
To Trust or Not To Trust, That Is… Expensive!
Just 41% of organizations in the study said they deploy a zero trust security architecture. The other 59% percent of organizations that don’t deploy zero trust incur an average of $1M in greater breach costs compared to those that do deploy. Among critical infrastructure organizations, an even higher percentage of 79% doesn’t deploy zero trust. These organizations experienced on average $5.40M in breach costs, more than $1M higher than the global average.
Alright Everyone… Back To The Office!
When remote working was a factor in causing the breach, costs were an average of nearly $1M greater than in breaches where remote working wasn’t a factor — $4.99M versus $4.02M. Remote work-related breaches cost on average about $600K more compared to the global average. Back in 2020 I remember when they added $150K in a guesstimate for the impact of all the remote work conversion on data breach costs. Looks like that number may have been way off.
But I’m In The Cloud, So I’m OK… Right?
45% of breaches in the study occurred in the cloud. Yet breaches that happened in a hybrid cloud environment cost an average of $3.80M, compared to $4.24M for breaches in private clouds and $5.02M for breaches in public clouds. The cost difference was 27.6% between hybrid cloud breaches and public cloud breaches. Organizations with a hybrid cloud model also had shorter breach lifecycles than organizations that solely adopted a public or private cloud model.
Failing To Plan Is Planning To Pay
[32:14] Nearly three-quarters of organizations in the study said they had an IR plan, while 63% of those organizations said they regularly tested the plan. Having an IR team and an IR plan that was regularly tested led to significant cost savings. Businesses with an IR team that tested its IR plan saw an average of $2.66 million lower breach costs than organizations without an IR team and that don’t test an IR plan. The difference of $3.26M versus $5.92M represents a 58% cost savings.Extended Detection & Response = Much Fast Response
Those organizations with XDR technologies deployed shortened the breach lifecycle by 29 days! This is not a surprising number though. The tools are designed to improve detection and response times. If they weren’t at least this much better at it, the costs would likely not be worth it. I think we will see that number climb as deployments are increased and the tools are perfected.
Initial Attack Vectors
In 2022, the most common initial attack vectors were compromised credentials at 19% of breaches, phishing at 16% of breaches, cloud misconfiguration at 15% of breaches and vulnerability in third-party software at 13% of breaches. The 2021 report saw the same order of the top four initial attack vectors. The costliest initial attack vector in 2022 on average was phishing at $4.91M. Following phishing was business email compromise at $4.89M and 6% of breaches, vulnerability in third-party software at $4.55M and compromised credentials at $4.50M.
Types of breaches they found were what you would expect.
Key Cost Factors
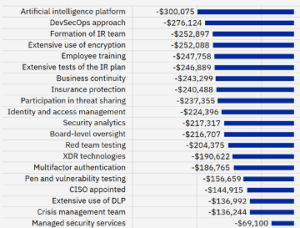
[37:59] This is an area that provides stats we work from regularly. It just seems logical that the items that make a breach more expensive should be mitigated and things that make it less expensive should be improved or implemented.New cost factors were included this year: IAM; XDR technologies; MFA; and crisis management teams. However, the usual suspects are in the mix still.
$5.57M is the average cost of a breach for organizations with high levels of compliance failures.
So, here is the focus on what makes it less expensive
And what makes it more expensive.
It’s A Risk Management Decision!
[45:59]Chief information security officers (CISOs), risk managers and security teams can use benchmark research like the Cost of a Data Breach Report to infer general trends and cost averages in their industry or geography. However, using data specific to the organization, rather than industry averages, can clarify potential security gaps and how to reduce overall risk by quantifying security risk into financial terms.
Wow! That sounds like doing a risk analysis, assessment and risk management plan. Maybe that is why regulated industries’ costs are in the longtail.
For those of us in the HIPAA-sphere, when the study refers to risk quantification, they are basically talking about a risk analysis, risk assessment and risk management plan. So if you are following HIPAA and creating and maintaining your privacy and security risk based program the right way (like we teach you at the PriSec Boot Camp on Mar 12, 13, 14 & 15th, 2023 in Louisville, KY), then it should provide you with substantial savings on the cost of a data breach.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
HIPAA is not about compliance,
it’s about patient care.TM
Special thanks to our sponsors Security First IT and Kardon.