Today, we are going to give you our six takeaways from the 15th annual Verizon Data Breach Investigation Report. We like these reports because they give us an indication of what’s going on in the cyber world, what we need to be looking for and looking out for.
Today, we are going to give you our six takeaways from the 15th annual Verizon Data Breach Investigation Report. We like these reports because they give us an indication of what’s going on in the cyber world, what we need to be looking for and looking out for.
In this episode:
6 Takeaways 2022 Verizon DBIR – Ep 359
Today’s Episode is brought to you by:
Kardon
and
HIPAA for MSPs with Security First IT
Subscribe on Apple Podcast. Share us on Social Media. Rate us wherever you find the opportunity.
The Privacy and Security Boot Camp
3.5 day In Person Event
Sep 12, 13, 14 and 15
PriSecBootCamp.com
Great idea! Share Help Me With HIPAA with one person this week!
Learn about offerings from the Kardon Club
and HIPAA for MSPs!
Thanks to our donors. We appreciate your support!
If you would like to donate to the cause you can do that at HelpMeWithHIPAA.com
Like us and leave a review on our Facebook page: www.Facebook.com/HelpMeWithHIPAA
If you see a couple of numbers on the left side you can click that and go directly to that part of the audio. Get the best of both worlds from the show notes to the audio and back!
HIPAA Say What!?!
[05:53] HIPAA requires multiple types of training including Security Awareness training.Security Rule: 45 CFR 164.308(a)(5)
Standard: Security awareness and training. Implement a security awareness and training program for all members of its workforce (including management).
Implementation specifications: Security reminders (Addressable). Periodic security updates.
Privacy Rule: 45 CFR 164.530(b)
Standard: Training. A covered entity must train all members of its workforce on the policies and procedures with respect to protected health information required by this subpart and subpart D of this part, as necessary and appropriate for the members of the workforce to carry out their functions within the covered entity.
Implementation specifications: Training.
(i) A covered entity must provide training that meets the requirements of paragraph (b)(1) of this section, as follows:
(A) To each member of the covered entity’s workforce by no later than the compliance date for the covered entity;
(B) Thereafter, to each new member of the workforce within a reasonable period of time after the person joins the covered entity’s workforce; and
(C) To each member of the covered entity’s workforce whose functions are affected by a material change in the policies or procedures required by this subpart or subpart D of this part, within a reasonable period of time after the material change becomes effective in accordance with paragraph (i) of this section.
(ii) A covered entity must document that the training as described in paragraph (b)(2)(i) of this section has been provided, as required by paragraph (j) of this section.
Periodic does not mean “once a year.” But this is so easy. There is lots of free information online you can use to provide periodic security reminders. The good news for you podcast listeners is that you can sign up for David’s mailing list that provides weekly security reminders and updates. You don’t have to be a client of his company to get on the mailing list. Just send him an email at David@HIPAAforMSPs.com and he will add you to the list. You can use these security tips and reminders as security awareness training for your staff.
405(d) Tip of the Week
[14:11] Another great place where you can get information for security reminders is through the 405d team. Their social media sites and website have excellent training information and they even have a recent post on how to create training programs.So, for our 405d tip of the week, we continue our review of the 10 best practices to help mitigate the top 5 threats facing the healthcare and public sector.
Practice #6: Network Management:
You can download the Network Management Poster from the 405d website.
For Small Organizations:
- Network Segmentation: Configure networks to restrict access between devices to that which is required to successfully complete work. This will limit cyberattacks from spreading across your network.
- Physical Security and Guest Access: Just as network devices need to be secured, physical access to the server and network equipment should be restricted to IT professionals. As much as possible, limit the ability of your workforce to access guest networks.
- Intrusion Prevention: Implement intrusion prevention systems as part of your network protection plan to provide ongoing protection for your organization’s network. Most modern firewall technologies that are used to segment your network include an intrusion prevention systems (IPS) component
For Medium/Large Organizations:
- Establish Network Profiles and Firewalls. An effective network management strategy includes the deployment of firewalls and network profiles to enable proper access inside and outside of the organization.
- Implement Web Proxy Protections. Web proxy systems provide important protections against modern phishing and malware attacks.
- Utilize Network Access Control systems. NAC systems are engineered to automatically profile new IT assets that connect to network resources, such as wireless networks, wired networks, or VPN.
6 Takeaways 2022 Verizon DBIR
[22:00] The 2022 Data Breach Investigations Report | Verizon (their 15th Annual DBIR) was released recently. As we always like to do, we review it for you and today are going to give you our top six takeaways. You can get your own copy of the report by clicking the link above.The DBIR team analyzed 23,896 incidents, of which 5,212 were confirmed data breaches. Now, let’s start by reminding everyone that there is a difference between an incident and a data breach. You should teach your staff to say “we have an incident” not “we have a breach.” They are very different and could cause undue confusion and uncertainty of your security safeguards.
Takeaway #1
- Credentials
- Phishing
- Exploit vulnerabilities
- Botnets
These four pervade all areas of the DBIR, and no organization is safe without a plan to handle them all.
[28:36] Takeaway #2:
[30:22] Takeaway #3:
The human element is big and it is the hardest to prevent. There are three pieces to the human element. You have those who cause harm:
- Accidentally – People make mistakes. We all are human. There is no malicious intent to cause harm.
- With Malicious Intent – People make a decision to do something, knowing it will cause harm in some way.
- Unintentionally – The scariest ones are the ones. They do not intend for there to be a data breach, but they make a decision to take the action anyway.
But that’s where security awareness training for all staff members comes in. You can’t just hire IT or throw technology at trying to fix this part. You have to invest resources to train your workforce on security awareness topics to have a fighting chance to help reduce your exposure to a data breach. We talk about training alot but we covered this topic in a very early episode of our podcast – HIPAA Security Awareness: It’s the People, People – Ep 20, back in Sep 2015. It is still relevant today and part of your security program that is often ignored.
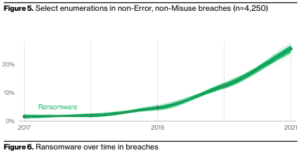
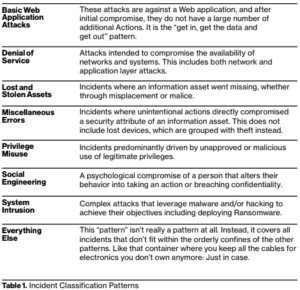
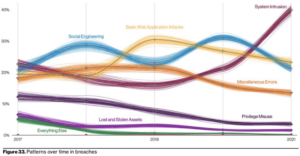
[34:55] Takeaway #4The Verizon DBIR report breaks the incidents into 8 categories. The chart below shows the 8 patterns and how they are defined.
The ones that are most prevalent these days are:
- System Intrusion
- Basic Web Application Attacks
- Social Engineering
Complex attacks that leverage malware and/or hacking to achieve their objectives including deploying Ransomware.
These attacks are against a Web application, and after initial compromise, they do not have a large number of additional Actions. It is the “get in, get the data and get out” pattern.
A psychological compromise of a person that alters their behavior into taking an action or breaching confidentiality.
Great news for healthcare! Insiders are not the top concern like they had been for years.
They took the time for each of the industry segments to include Internet Security (CIS) Critical Security Controls) to prioritize in each industry section to help set priorities based on the data. The healthcare recommendations were:
- Security Awareness and Skills Training (CSC14),
- Secure Configuration of Enterprise Assets and Software (CSC 4),
- Access Control Management (CSC 6)
There is a special report for SMBs and this year it includes specific discussions about Very Small Businesses. A few special points on it:
There is a great list of recommendations for these organizations to use. Much of it is information we have covered many times before. One of the best points it recommends is to have a plan.
Some planning on your part, along with a bit of educating the people most likely to encounter these kinds of attacks, can go a long way in helping to make your small company safer.
Other resources shared for these businesses include Scam Spotter and Fightcybercrime.org. These two have some very interesting stuff, definitely worth checking out yourself and sharing with your IT team.
There is a lot of information in these reports every year. Take the time to check them out for yourself and you will certainly gather additional takeaways from them.
Remember to follow us and share us on your favorite social media site. Rate us on your podcasting apps, we need your help to keep spreading the word. As always, send in your questions and ideas!
HIPAA is not about compliance,
it’s about patient care.TM
Special thanks to our sponsors Security First IT and Kardon.